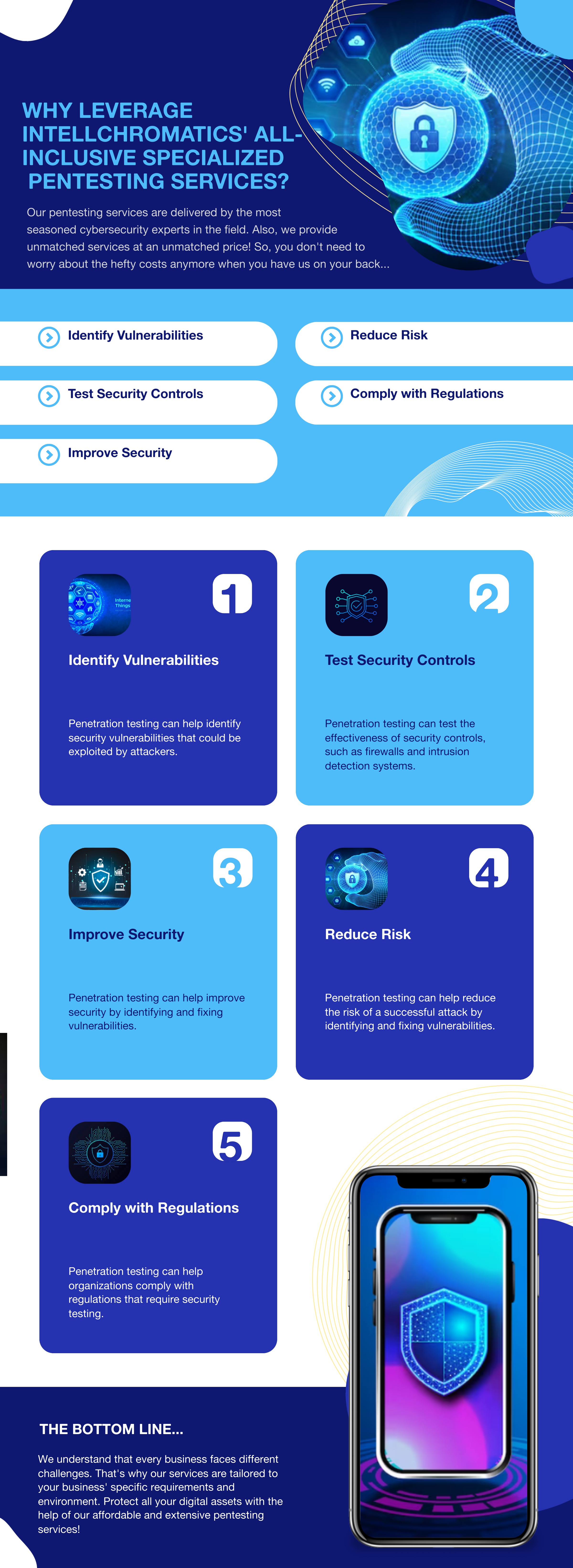
PREMIUM 360° Comprehensive Pentesting
As a provider
of in-depth security evaluations, we find flaws that endanger your company
and offer recommendations on how to fix them. To become the greatest
penetration testing company in the market, we combine industry-leading
security engineers, exclusive technology, and security research. We thus
have the experts to meet your specific demands, whether they are related to
social engineering testing, sophisticated online applications, the AWS
cloud, or the external network. To suit your demands, we provide a variety
of penetration testing services. We have the experts to handle any kind of
penetration test, be it a cloud pentest, online application pentest, social
engineering evaluation, or something more unusual.
Our Patrons Have Assured Security
Depending on the sector and organizational objectives, different security
goals and requirements apply. A hospital's requirements are much different
from a university's threat model. We adapt to your specific demands, taking
into account these peculiarities.
We take your team through every step of the attack narrative and the
underlying threats at the end of our penetration testing services. You have
the concrete, workable ways to strengthen your security posture, all of
which are thoroughly explained in the pentest report.
Our Clients and Benefactors
From high-tech startups to bif corporations, our clientele comprises
security-aware businesses across a broad spectrum of sectors and
requirements. We make certain that every pentest achieves the client's
goals by first comprehending the fundamental causes. We align every
assessment to the demands of the company, from SOC2 and vendor
requirements to security code review prior to a launch.
We are your committed security partner, and our help doesn't stop with the
penetration test result. We are always here to offer advice.
Unrivaled Security Knowledge
Being a skilled attacker is frequently necessary to avert attacks, since the best defense is a solid offensive. Our firm focuses solely on offensive security and pen testing, with a sophisticated attack capability. To better serve our clients, we're always trying to enhance our skills, which ranges from creating our own malware and toolkits to reverse engineering equipment.
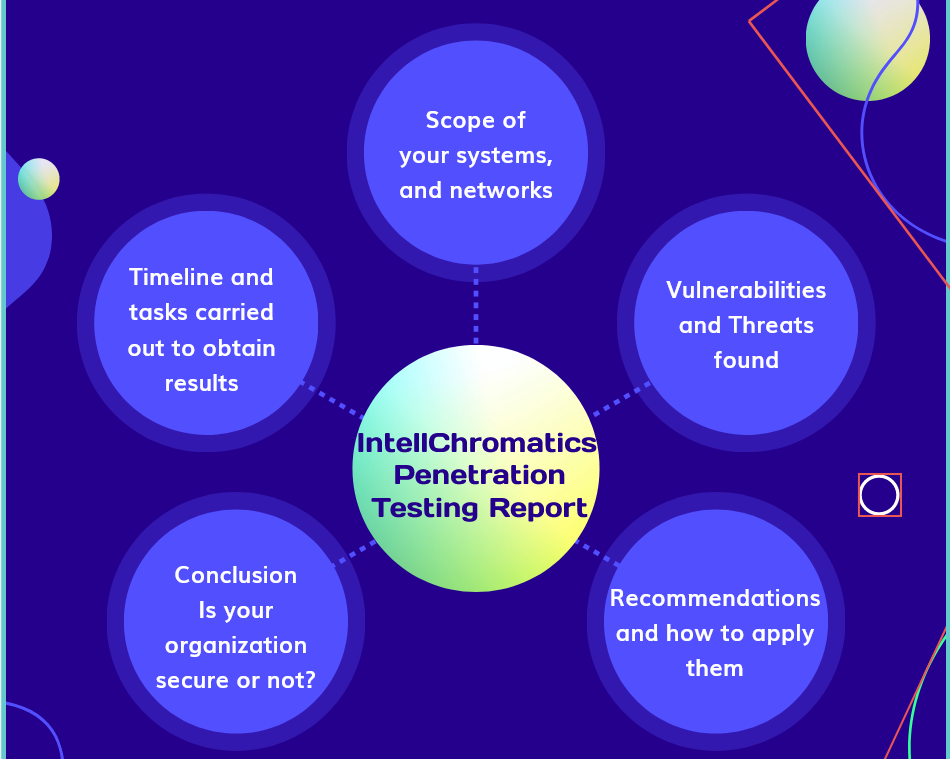
Professional and Sophisticated Pentest Report Documentation
Choosing a provider involves more considerations than just technical proficiency and research capacity. The final paperwork, which is commonly sent to your management, coworkers, and clients, and the penetration test result are crucial. We take great satisfaction in our polished, expert format and have outstanding reporting skills.
Technical Depth and Research
We are proud of
our penetration test results and documentation. Our reports, which are
tailored to the requirements of both technical engineers and senior
leadership, succinctly present risk summary and vulnerability information.
We are continuously studying, creating, and breaking as we relentlessly
pursue new concepts. Every pentester participates in research to stay
current with emerging trends. We don't simply utilize the tools; we
create them. We have hundreds of zeroday vulnerability releases and a
cache of internally generated scripts.
Ready to challenge your Information
Security systems?